Top 5 Cloud Security Issues Experienced with SaaS and It’s Solutions
Cloud computing has changed the IT approach, enabling it to become more agile, introduce new business models, provide more services, and reduce IT costs. Cloud computing technologies can be implemented in a wide variety of architectures under different service and deployment models and work together with other technologies and software design approach.
With the passage of time, cyber attacks have become very frightening. No matter what business you are in today, be it an eCommerce business or a non-profit organization or a call center, one needs to be very safe and free from cyber attacks. Therefore, security issues need to be addressed.
Although organizations are more willing to encourage team collaboration and increase productivity, one aspect that is very important is that all of these also increase the risk of cyber threats and attacks. It is therefore important that all companies must follow strict standards to maintain safety.
Some of the issues are as discussed:
1. Visibility issue
The first issue that most organizations face is the adoption of a zero-trust security architecture that can protect data in the cloud. The data must be fully secured and have a zero-trust security policy and each must verify who they are before gaining access to the resources and data stored in the cloud app. Some of the approaches are Single Sign-On (SSO) and Multi-factor Authentication (MFA).
The advantage of multi-factor authentication is that, in most cases, it’s very secure. The combination of a password, physical token, and biometric can significantly reduce the risk of data and software breaches. SSO is more convenient for users but has higher inherent security risks.
2. Security and unauthorized access
Today in this digital age all over the world can be reached at the click of a button and mobile phones and iPads are scattered in the market. Therefore, cybersecurity is very important as most employees log into cloud solutions from their mobile phones, home tablets, and home desktop PCs, making the system vulnerable to many external threats. Therefore it is very important to see that employees also do not become negligent, and they don’t access in an unauthorized manner.
In some cases, public cloud security is at risk due to a lack of visibility and may lead to unauthorized access to data, improper handling, and replication of data to remove confidential data from the infrastructure. This can affect an organization’s ability to verify the effectiveness of their security controls (as there is no visibility into the data of the equipment and the cloud). Pentesting or vulnerability assessment is the best way to exploit vulnerabilities in a system to determine whether unauthorized access or other malicious activity is possible and identify which flaws pose a threat to the application.
3. Data security
Data security is one of the most crucial as protecting your company’s data is critical. Cloud storage with automated backup is scalable, flexible, and provides peace of mind. A decade ago, enterprise data typically resided in the organization’s physical infrastructure, on its own servers in the enterprise’s data center, where one could segregate sensitive data in individual physical servers. Today, with virtualization and the cloud, data may be under the logical control of organizations, but physically resides in infrastructure owned and managed by another entity.
By its very nature, cloud computing involves some control from customer to service provider. While this leaves users with more time and financial resources to focus on other aspects of the business, there is always a risk that sensitive data is in someone else’s hands. If the security of the cloud service is breached, hackers could potentially gain access to intellectual property or other personal files.
Various data loss prevention solutions, SaaS security, and malware threat protection can all increase the cloud data security to reduce the risk of internal and external threats and guard against data breaches.
4. Accidental Data Breaches
Human error is the most common source of a data breach, and proactiveness is the key to prevention. To ensure costly mistakes are not made, help employees understand how and where data breaches can happen. Accidental data breaches are often compounded by an organizational failure to encrypt data prior to it being shared – both internally and externally – putting their organizations at risk of non-compliance with major data privacy regulations.
This is largely driven by the explosive growth in unstructured data (emails, documents, files, etc.), combined with the growing number of ways employees can communicate internally and externally.
5. Inability to monitor data in transit to and from cloud applications
For securing data at rest, cryptographic encryption mechanisms are certainly the best options. The hard drive manufacturers are now shipping self-encrypting drives that implement trusted storage standards of the trusted computing group. These self-encrypting drives build encryption hardware into the drive, providing automated encryption with minimal cost or performance impact.
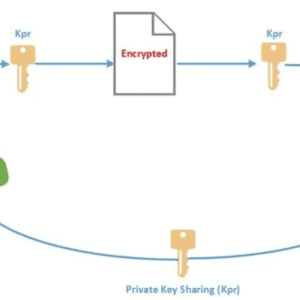
Although software encryption can also be used for protecting data, it makes the process slower and less secure since it may be possible for an adversary to steal the encryption key from the machine without being detected.
Encryption is the best option for securing data in transit as well. In addition, authentication and integrity protection mechanisms ensure that data only go where the customer wants it to go and it is not modified in transit. Strong authentication is a mandatory requirement for any cloud deployment. User authentication is the primary basis for access control. In the cloud environment, authentication and access control are more important than ever since the cloud and all of its data are accessible to anyone over the Internet. The trusted computing group (TCG) IF-MAP standard allows for real-time communication between a cloud service provider and the customer about authorized users and other security issues.
One can also opt for best-in-class cloud malware threat protection technology which is the optimal way to protect against malicious attacks.
Final Verdicts
The security concerns associated with cloud computing do not extend beyond the benefits of moving your business to the cloud.
Even though digital transformation is fueling, it is seen that the widespread adoption of cloud computing by organizations helps them innovate.