How and Why Facial Recognition Technology is Safe
What is facial recognition, or face recognition, or FaceCheck ID for short? What is the process of facial recognition? What potential uses does it have in real life? One of the most popular identifying methods for online identity verification is biometric facial recognition.
Find out more about each of the subjects covered in this article.
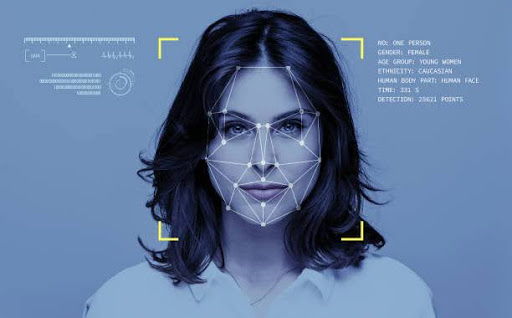
What is a FaceCheck ID? What Face Recognition is and How It Functions
FaceCheck ID, by definition, is the technology that can recognize or authenticate a subject based on his face in a photograph, video, or other audiovisual component. This identity functions similarly to a face scanner and is typically used to get access to a system, application, or service.
It is a biometric identification technique that makes use of certain bodily measurements—in this example, the face and head—to confirm an individual’s identity using their facial biometric pattern and data. To identify, validate, and authenticate a person, the technology gathers a collection of distinct biometric data linked to their face and facial expressions.
Software for FaceCheck ID
To construct and record the biometric facial pattern of the person who has to be identified, any device with digital photography technology must be able to make and obtain the images and data required for the face identification operation.
Biometric facial recognition is one of the safest and most efficient methods of identification since it uses special mathematical and dynamic patterns that function like a face scanner, unlike other methods like passwords, email verification, verification through selfies or photos, or fingerprint identification.
Finding a succession of photographs with the same face from an incoming image in a database of training images is the aim of face recognition. Ensuring the real-time execution of this process poses a significant challenge, as not all biometric face recognition software suppliers can offer it.
And how does face recognition get used? Two variations of the facial recognition procedure can be executed based on the timing of the operation:
The first one is where a face is recognized by a facial recognition system for the first time to register it and link it to an identity so that it is stored in the system. Another name for this procedure is “digital onboarding with Facecheck.id.
the version where users must first authenticate themselves before registering. The method involves comparing the data received from the camera with the data already stored in the database. The user is given access to the system with his login credentials if the face matches an identity previously recorded.
The greatest safety and dependability requirements can be met by facial recognition systems thanks to the application of artificial intelligence (AI) and machine learning technology. Likewise, the combination of various algorithms and computing techniques allows the process to be executed in real time.
How Is Face Recognition Operated?
How to use Facecheck ID Instagram? To what extent is facial recognition accurate? How does facial recognition operate? Depending on the features of the device, face recognition systems either capture an incoming image from a camera device in two dimensions or three dimensions.
These are far more dependable and safe than the information gleaned from a static image since they compare the important data of the incoming image signal in real-time in a picture or video in a database. Since the database is hosted on servers and cannot be found on the capture equipment, the biometric facial recognition technique requires an internet connection.
It checks that the biometric data matches the individual requesting access to a system, application, or even building, and it mathematically analyzes the incoming image in this face comparison without any margin of error.









